OPS345 Lab 6 - HTTPS
Public-key Cryptography
The most common implementation of public-key cryptography (also known as asymmetric encryption) is RSA, which is named after its inventors: Ron Rivest, Adi Shamir and Leonard Adleman. RSA involves a public key and a private key. The public key can be known by everyone and is used for encrypting messages. The intention is that messages encrypted with the public key can only be decrypted in a reasonable amount of time by using the private key.
This is the foundation that all modern encryption is built on. You have been using it all semester (and in OPS245) to generate RSA key pairs to use SSH (for remote access between systems) without a password. In Lab 6 you will use it to secure your Apache web server with TLS/SSL (HTTPS).
HTTP is a protocol or set of communication rules for client-server communication over any network. HTTPS is the practice of establishing a secure TLS/SSL protocol on an insecure HTTP connection. Before it connects with a website, your browser uses TLS to check the website's TLS or SSL certificate. TLS and SSL certificates show that a server adheres to the current security standards. You can find evidence about the certificate within the browser address bar. An authentic and encrypted connection displays https:// instead of http://. The additional s stands for secure. The term SSL certificate is still commonly used in industry even though everything uses TLS.
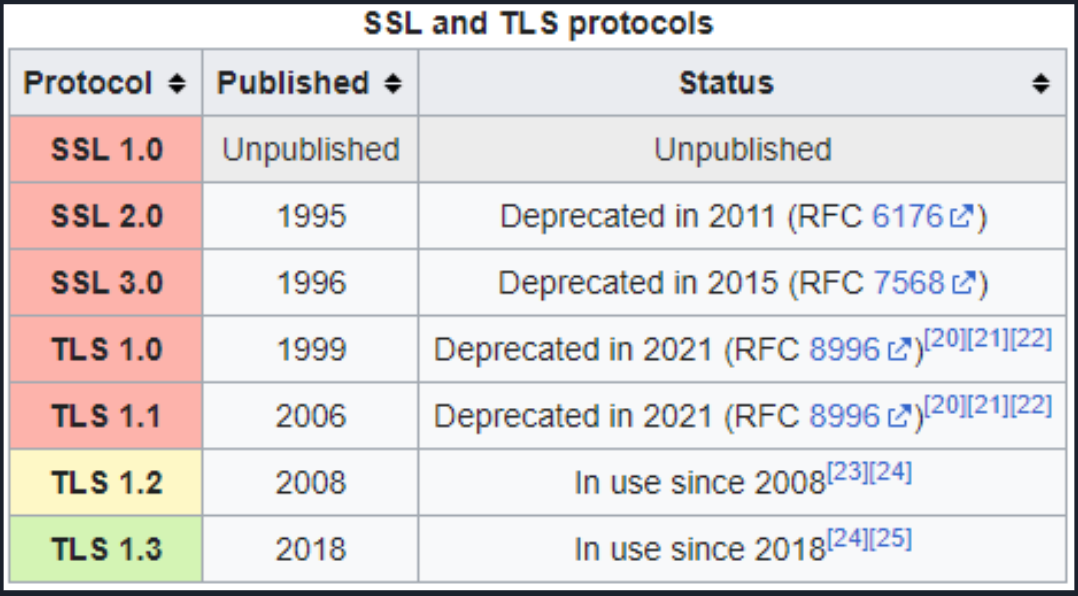
SSL was first released in 1995 as SSL version 2 (version 1 was never published). TLS is the successor to SSL. It first released in 2006. All versions of SSL have been formally deprecated. TLS versions 1.2 and 1.3 are supported. The following is a list of SSL & TLS standards.
Preparation
Remove the load balancing rules you added to your router instance in Assignment 1, as they will cause issues. For this lab, add a single rule port forwarding incoming traffic from port 80 to www. Perform the rest of this lab on www.
Certbot
Certbot is a free, open source software tool for automatically using Let's Encrypt certificates on manually-administrated websites to enable HTTPS. Certbot is made by the Electronic Frontier Foundation (EFF), a 501(c)3 nonprofit based in San Francisco, CA, that defends digital privacy, free speech, and innovation. Reference
You are going to install Certbot, which will automate configuring HTTPS using Let's Encrypt.
Installing Certbot
Start the learner lab and login to your www instance.
First, you will need to install some dependencies. Run the following commands to install the dependencies.
sudo dnf install python3 augeas-libs mod_ssl
Issue the following commands to set up a virtual environment in Python
sudo python3 -m venv /opt/certbot/ sudo /opt/certbot/bin/pip install --upgrade pip
Install Certbot with the following command.
sudo /opt/certbot/bin/pip install certbot certbot-apache
Issue the following command to ensure certbot can be run.
sudo ln -s /opt/certbot/bin/certbot /usr/bin/certbot
Configuring an Apache Virtual Host
Create the file /etc/httpd/conf.d/yourdomainname.conf. Substitute your domain name for jason.carman in the example command.
sudo vi /etc/httpd/conf.d/www.jason.carman.ops345.ca.conf
Enter the following contents, and save.
<virtualhost *:80> ServerName www.jason.carman.ops345.ca </virtualhost>
Generating the TLS/SSL Certificate
Issue the following command to generate a certificate, automatically include it in your apache configuration and enable HTTPS.
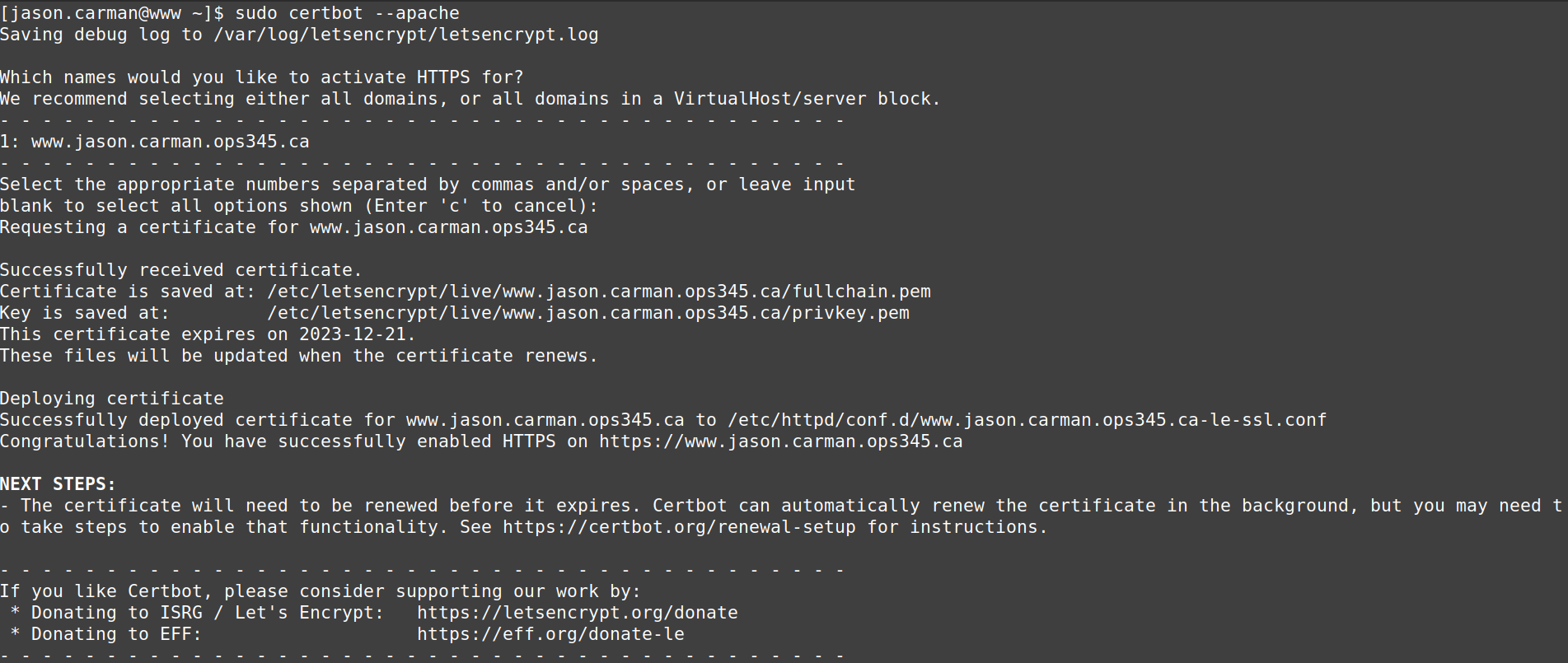
sudo certbot --apache
Accept the terms of service. Answer as you wish for sharing your email, then enter your domain name. See the following example.
Automate your certificate renewal using cron.
echo "0 0,12 * * * root /opt/certbot/bin/python -c 'import random; import time; time.sleep(random.random() * 3600)' && sudo certbot renew -q" | sudo tee -a /etc/crontab > /dev/null
Try accessing your web server in a browser using https. You may need to modify your www security group to allow incoming https traffic from anywhere (0.0.0.0/0).
Submission
Show your professor a screenshot showing your webpage accessible through a browser using HTTPS.